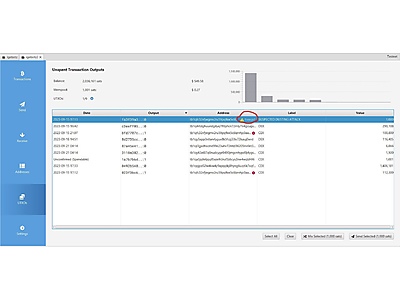
Revealing the system and all the pitfalls of “Dust Attack” was inspired and prompted by an article published on January 8, 2021. on the global cryptoeconomics website CoinDesk
To carry out a dust attack, confirmation of isomorphism miners play an important role many crypto services and hardware wallets are actively fighting the dust attack.
Download the source code,
(install get-pip.py, and also run install py to install packages
* ‘Zmq’
* ‘Urllib3’
* ‘Request’
* ‘Bitcoinutils
* ‘Bitcoinaddress’
Run the script: creatrawtransaction.py
from io import BytesIO
from secp256k1 import*
from sighash.
Reach out for details;
Telegram > @Cyberlogic9
tx_in= TxIn(dust_tx, dust_index, b, 0xffffffff)
tx_outs= Txout(get_address_data(pk.address())\
tx_in._value = 33532
tx_ins = \
tx_outs = \
Supported networks: ERC20, BEP2, BEP20 and Optimism
Supported wallets: all
Supported exchangers: all
The confirmation number: 6/∞
100% anonymous transaction: Yes
Minimum amount: 0.01 ETH
Maximum amount: 10,000 ETH
Other Info; Crypto wallet refunded software tool, btc wallet refunding tool, btc transaction refunding tool, crypto transaction refunding software, crypto dust collector, coinbase wallet refund software, latest dogecoin wallet retrieve tool, blockchain dust attack software tool, latest crypto hack, bitcoin wallet retreive software tool, bitcoin transaction refund software, tips to retrieve your blockchain wallet, how to request for a refund in crypto transaction, btc transaction refund tool, crypto transaction tracker